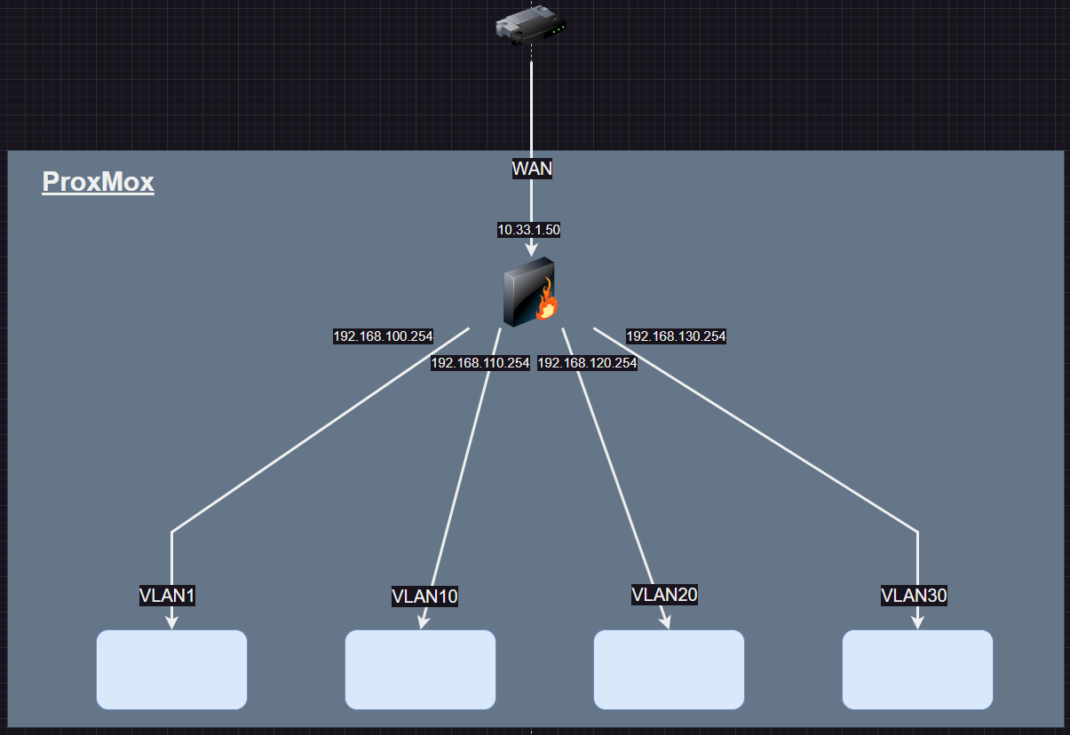
Overview The cybersecurity field is so vast and is ever evolving that staying current is a struggle. This struggle applies to both red teamers and defenders alike. In today’s day and age, there are plenty of platforms that provide virtual environments that allow users to test and develop their skills. But what happens when these platforms do not have a virtual environment that fits a very specific use case or scenario? Say, for example, a new vulnerability drops. If you are a red teamer, you may want to develop an exploit that would provide remote code execution. If you are…
Enumeration As with every engagement, it starts with information gathering. Ran the standard nmap scan and found the following port open on the target system. A scan for UDP ports was also done but nothing interesting was seen. Initial Access The first thing I did was see if there was any low hanging fruit by performing a simple brute force against TCP port 22. Unfortunately, no credentials were found so moved on to TCP port 80. Simply navigating to the target system’s IP in the browser revealed that there should be some sort of ticketing system that is only accessible…
The Journey Back in May 2022 I made a post about starting my OSCP journey. The intent, at the time, was to use open source resources such as Hack the Box and TryHackMe to help prepare prior to enrolling in Offensive Security’s PEN-200 course. Well, life had other plans because shortly after the journey started it had to be put on pause. More important and pressing responsibilities took up most, if not all, of my free time. It was not until August 2023 when the journey was able to be resumed. At that point it was decided to dive into…
Enumeration As with every machine, I like to start off with an nmap scan of all TCP ports using the standard NSE scripts and gather version information. Additionally, I did a scan of the top UDP ports. The results of the scans show TCP ports 22, 80, 8338, and 55555 as open as well as UDP port 68 being open. Looking closer at the results, TCP ports 80 and 8338 are showing as filtered. This means there is a firewall or filter in place that is preventing a successful connection from the attack box to the target box. Initial Access…
Introduction This box taught me a lot. It provided many opportunities to learn how to enumerate services, even if nothing ultimately was gleaned from it. It also taught me that sometimes getting fresh air and resetting is the best thing to do. Sometimes you need to try harder, but that is not always the case. And finally, do not get stuck on using the same tools or wordlists for a specific job. Different tools can give different results, so expand your arsenal. Sometimes you might not get results because of the tool, not because of something you are inherently doing…
But wait, there’s more! In the previous post I showcased how VBScript can be ran via LNK files. This post will discuss how LNK files can be weaponized to run DLLs via PowerShell. Macro-Enabled Office Documents Are Overrated There has been a recent shift in Emotet and IcedID campaigns that utilize ZIP or ISO files, instead of Microsoft Office documents, as their lure to distribute malware. Within these ZIP/ISO files are a LNK file and stage 1 DLL. When a user double clicks the LNK file, it launches the stage 1 DLL which downloads the second stage. Typically this leads…
Introduction It is a common tactic for malicious cyber actors to attain initial access to a victims’ computer through phishing campaigns. During these campaigns, Microsoft Office documents with malicious macros would typically be used to distribute malware. Unwitting users would enable macros and just like that malware is dropped on their machines. This TTP became so widely used that Microsoft decided to intervene around October 2022 and blocked macros, by default, on Office documents downloaded from the Internet. Unfortunately, malicious actors are not so easily defeated. What is the next best way to trick a user into installing malware on…
Learning on the Go All my cybersecurity experience up until this point in my career has been focused on the blue side of the house. But recently I was able to take what was learned over the years as a defender and apply that to a purple team. Simply said, a purple team is a mix of offensive (red) and defensive (blue) behaviors with the end goal of improving the overall security posture of an organization. Purple teams work closely with defenders to help train them, validate detection logic, and identify detection gaps. For quite some time I wanted to…
Learned a lot doing this box. It starts off with accessing an open SMB share that contains a password protected ZIP. Cracking the password for the ZIP allowed access to a PFX file. After cracking the password associated with the PFX file I was able to extract a .crt and .key file. Using those files, I was able to login via WinRM. After doing some recon on the local box I discovered a clear text password for another user in the PowerShell history file. Said user was part of a group that could read LAPS passwords. And it just so…
For this box, I discover a password protected ZIP file. After cracking the password and examining what was in the ZIP file, I find credentials to a website. Once logged in I discover that the HTTP application is vulnerable to SQL injection. I am able to exploit this vulnerability to get a reverse shell. Once on the box I take advantage of vi to get a shell as root thanks to GTFOBins! Initial Recon Started with the standard nmap scan. There are three ports open – SSH on 21, FTP on 22, and HTTP on 80. Initial Access FTP The…