This was an interesting box. It shows how information leaked by a HTTP application can aid an attacker in a password guessing attack. Creating an account in the web application revealed minimum password requirements. With that knowledge and assuming users do the bare minimum for password creation, I was able to create a custom password list. After a little bit of time and luck I was able to successfully guess a user’s password to gain access to the application.
Initial Recon
Started with the standard nmap scan.
┌──(crimson㉿crimson)-[~/HTB/Starting Point/Ignition]
└─$ sudo nmap -sC -sV -oA nmap/initial -p- -T5 $tgt
[sudo] password for crimson:
Sorry, try again.
[sudo] password for crimson:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-18 22:29 CDT
Warning: 10.129.83.194 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.129.83.194
Host is up (0.049s latency).
Not shown: 64745 closed tcp ports (reset), 789 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
|_http-title: Did not follow redirect to http://ignition.htb/
|_http-server-header: nginx/1.14.2
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 299.35 secondsThere is a single port open – HTTP on port 80.
Initial Access
HTTP
Per usual, I like to start Burp in the background to log the HTTP traffic. Next I attempt to navigate to the remote system’s IP. The response is 302 Found which tries to redirect my browser to ignition.htb. So I add that domain to be /etc/hosts.
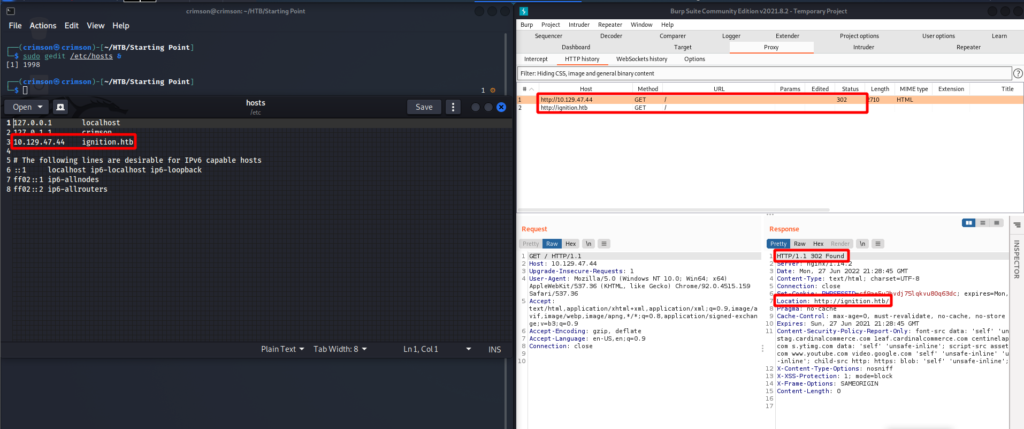
Before poking around on the HTTP application I started a gobuster scan in the background. The landing page tells me this application is some type of Content Management System (CMS). It seems to be a fresh install since it states “Default welcome msg!” in the upper right-hand corner of the page. There is also a login page and a way to create an account.
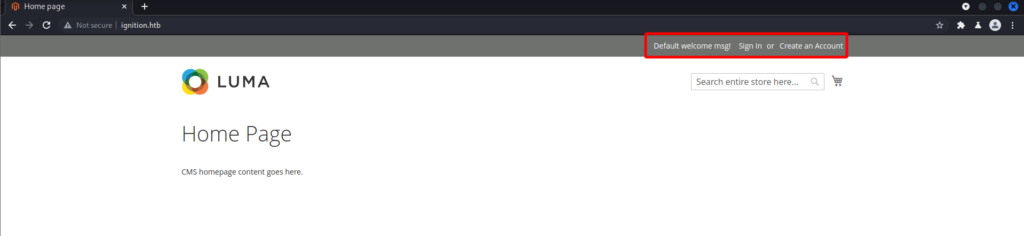
Going to the login page shows an email is needed for a username. At this point I have not seen an email on this web application so brute forcing does not seem feasible. But I can create an account so let me try that.
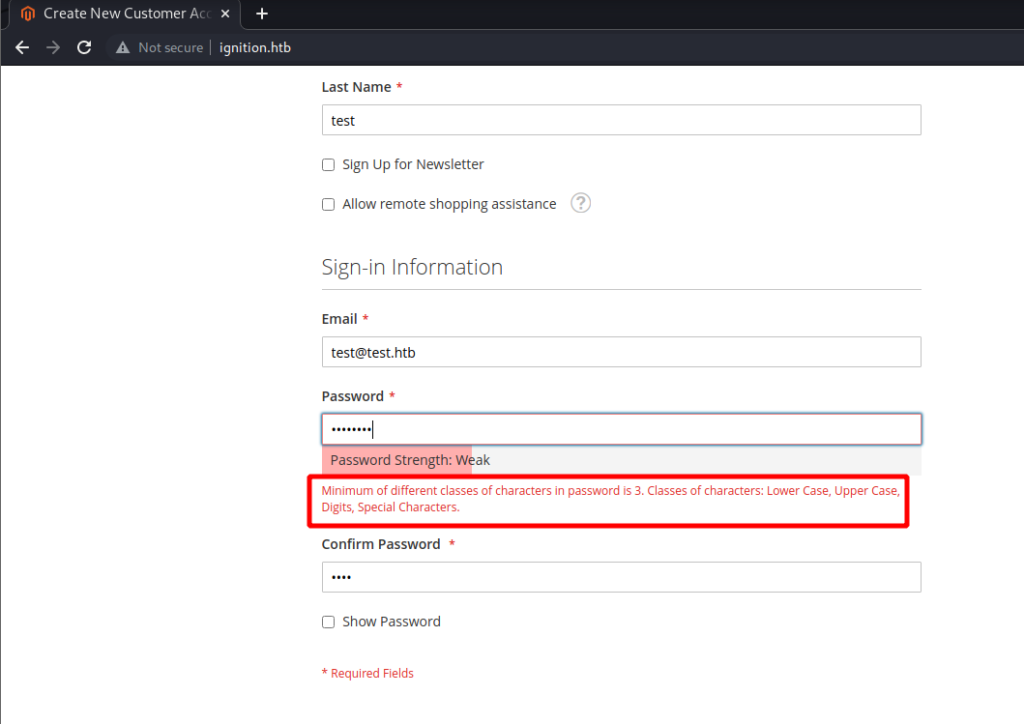
Trying to create an account reveals some interesting information. The password policy for this website requires a password minimum length of 8 or more characters.
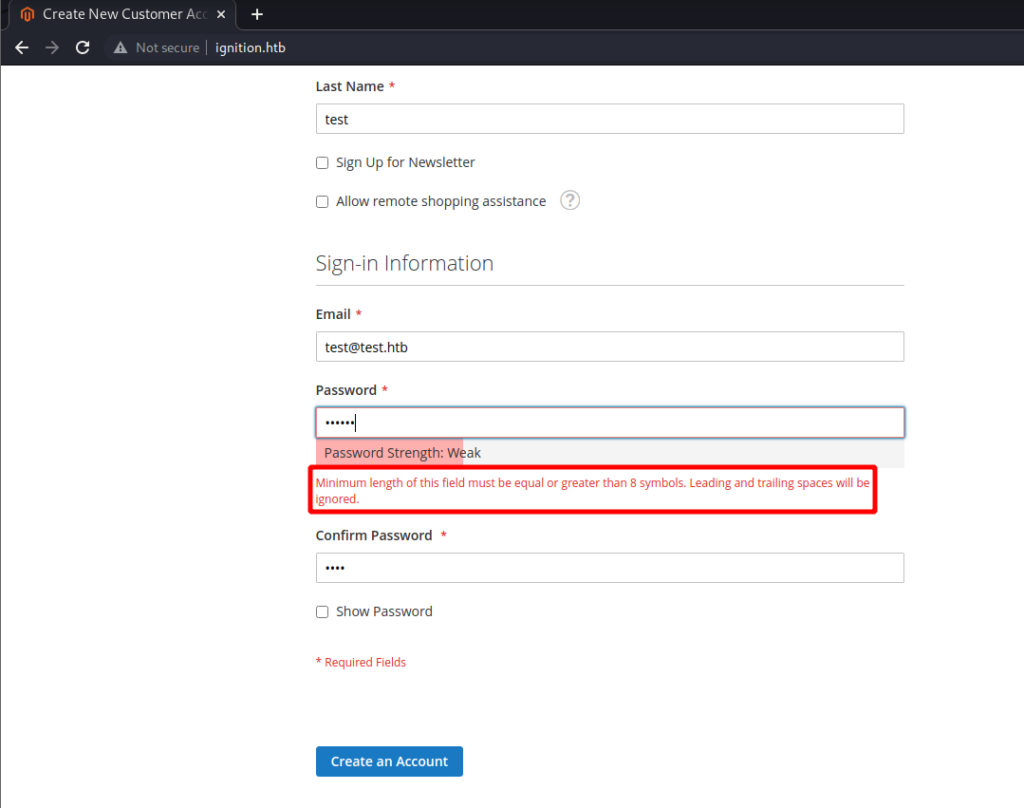
Then when I create a password with 8 characters I get even more information about the password policy. This information may prove useful for a password guessing attack.
After creating an account and logging in I poke around. On the face of it there does not seem anything too interesting.
But what about that gobuster scan? It seems as there there is a /admin directory so I check that out. When I do there is a different login page.
┌──(crimson㉿crimson)-[~/HTB/Starting Point/Ignition]
└─$ gobuster dir -u ignition.htb -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -o gobuster.root 1 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://ignition.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/SecLists/Discovery/Web-Content/raft-small-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/05/18 22:45:35 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 200) [Size: 7095]
/media (Status: 301) [Size: 185] [--> http://ignition.htb/media/]
/contact (Status: 200) [Size: 28673]
/catalog (Status: 302) [Size: 0] [--> http://ignition.htb/]
/checkout (Status: 302) [Size: 0] [--> http://ignition.htb/checkout/cart/]
/home (Status: 200) [Size: 25802] 
At first I try the standard usernames and passwords to no avail. Then I remember that information about the password policy was leaked when I created an account. So I need to create a password list that contain at least 8 characters with three different classes of characters. After looking for very common passwords that fit the criteria, it seems as though the username admin and the password qwerty123 works.